Are you a speedy shopper? Some companies are counting on you moving a little too quickly at checkout. Here’s why you should slow down and double check to avoid sneaky surprise charges.
Read MoreElon Musk has chosen you for his new investment project! But this Elon Musk is made up of pixels and crime. And he wants your money. The good news is he can help us detect other fakers like him. Here are the tell-tale signs that give away his deepfake voice.
Read MoreYou’ll find QR codes at restaurants, on receipts, and sometimes on the back of your cereal box. Do you ever scan them? Cyber crooks want to turn that habit into an illegal jackpot.
Read MoreWatch out for social media posts or ads touting apps that might do more harm than good. Researchers say digital sharks are finding their way onto official app stores and onto your phone. Here's how to steer clear of these dangerous waters so you don't get bitten.
Read MoreThe first wave of AI-written attack emails looks like this, researchers say. One of the first-known cases of computer-generated phishing hit six universities in the U.S.
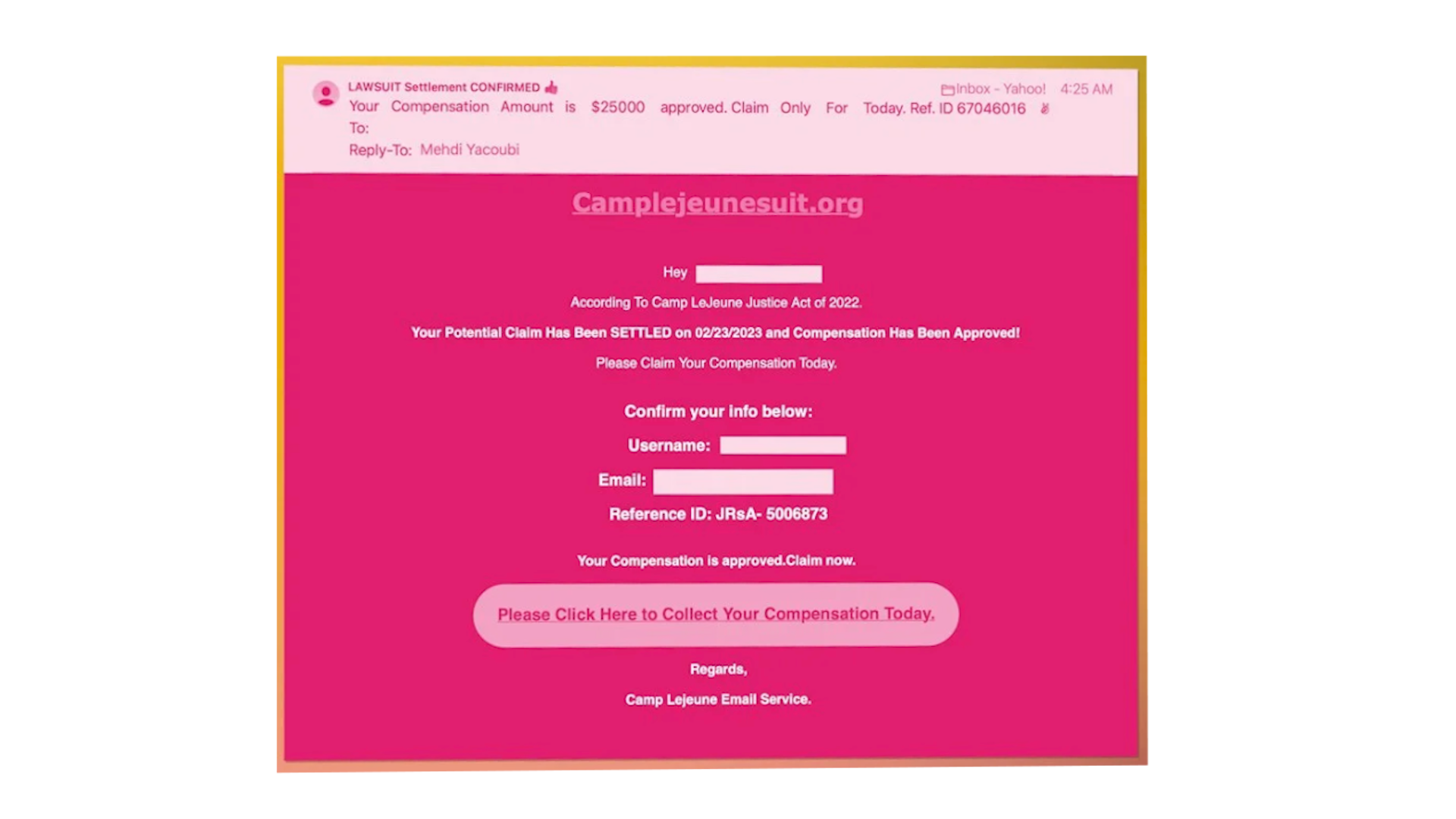
Read MoreCyber crooks have found an easy way to send you PayPal invoices that are both fake and real at the same time. The goal: to steal your money and take over your computer.
Read MoreHow do cyber attackers travel? They use airline miles. Sometimes yours. People are reporting a wave of airline account hacks, with points and money lost. Thieves are using you to run their own criminal travel agencies.
Read MoreThe battle to keep the power flowing in Ukraine plays out on two fronts, physical and cyber. That means while electricity workers are fighting cyberattacks, they’re also fighting to stay alive in the brutal war that has killed hundreds of thousands of people.
Read MoreCyber attackers can go undercover, hiding in your printer, to carry out attacks against you. Here’s what you can do to stop them.
Read MoreTechnology terms can sound like a bunch of mumbo jumbo. And in the case of the world-renowned encabulator, they don’t just sound made up. They really are! This joke machine now has a new chapter in its long, viral history.
Read MoreOne email. Two looks. Attackers are doubling their chances of tricking you with sneaky two-faced emails. Here’s how their scheme works.
Read MoreWatch out for fake email replies from cyber crooks who want to trick you into giving them your bank account. Here’s how the cyber scam works.
Read MoreIn a hybrid war of bombs and cyberattacks, cybersecurity experts are key. A Ukrainian cyber defender explains how she made it through the first year of Russia’s full-scale invasion of her country. .
Read MoreWe’re going undercover to expose the tactics of romance scammers who steal billions of dollars from people around the world. It begins with stolen pictures from one of the Village People and ends with a singing scammer and a slew of curses words.
Read MoreDoing a search online? Watch out for fake Google ads promoting fake sites that can steal your money and passwords to your bank account. In one case, the thieves hacked someone's accounts and helped themselves to a "life-changing" sum of money.
Read MoreYou think you're getting a refund. But cyber crooks are actually locking up your screen, digging into your bank account, and making off with your money --- all right in front of you. Here’s how the scheme works and how to protect yourself from fake refund scams.
Read MoreCyber attackers like to use malware to get into your computers, phones and networks. But it’s rare to see them creating malware specifically to target industrial machines, the ones that help keep our lights on, the electricity and water flowing, fuel and traffic lights. Here are two new pieces of industrial malware that got people’s attention in a big way.
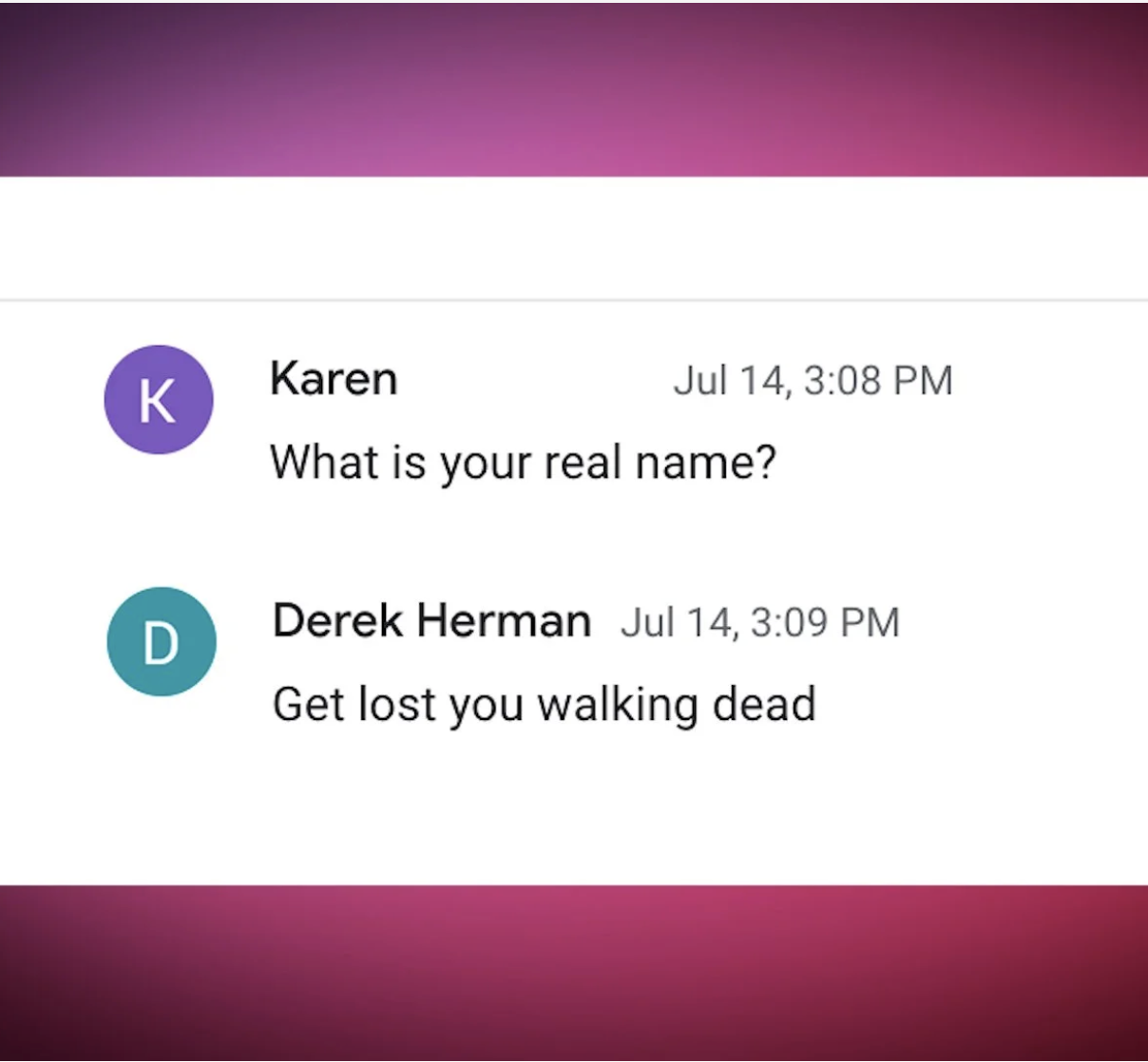
Read MoreAre you oversharing? Giving away too much about yourself on social media? A social engineering expert gives us three questions to ask yourself before you hit “publish.”
Read MoreYou may have heard that you shouldn't give sensitive information to people who call you on the phone. But what if you are the one calling them? Crooks know your guard is down. Here’s how they trick you into thinking you’re the one in control.
Read More